With the resurgence of the quantum threat theory, has the foundation of cryptocurrency been shaken?
Author|Azuma ( @azuma_eth )
Recently, the threat of quantum computing to cryptocurrencies has once again become a focus of discussion on the internet. This renewed interest stems from several key figures in the quantum computing and cryptocurrency industries publishing new predictions regarding the development of quantum computing and its potential capabilities.
First, on November 13th, Scott Aaronson, a leading figure in quantum computing and director of the Center for Quantum Information at the University of Texas, stated in an article : ” I now believe that we may have a fault-tolerant quantum computer capable of running Shor’s algorithm before the next US presidential election… ”

Then, on November 19, Ethereum co-founder Vitalik Buterin also spoke at the Devconnect conference in Buenos Aires, stating that elliptic curve cryptography (ECC) could be cracked by quantum computing before the 2028 US presidential election , and urged Ethereum to upgrade to quantum-resistant algorithms within four years.

What is the quantum threat?
Before interpreting Scott and Vitalik’s predictions, we need to briefly explain what the “quantum threat” is.
In short, the quantum threat to cryptocurrencies refers to the possibility that sufficiently powerful quantum computers in the future could break the cryptographic foundations that protect current cryptocurrencies, potentially destroying their security model.
Currently, the security of almost all cryptocurrencies (such as Bitcoin and Ethereum) relies on a technology called “asymmetric encryption,” the two most crucial components of which are the “private key” and the “public key”:
- Private key: kept secret by the user and used to sign transactions and prove your ownership of assets;
- Public key: Generated from the private key, it can be made public and used as part of a wallet address or address.
The cornerstone of cryptocurrency security lies in the fact that it is currently computationally infeasible to derive the private key from the public key. However, quantum computing may utilize the principles of quantum mechanics to significantly accelerate the process of solving certain mathematical problems by running specific algorithms (such as Shor’s algorithm mentioned earlier), which is precisely the weakness of asymmetric encryption.
Let’s continue explaining what Shor’s algorithm is. We won’t delve into the overly mathematical details here, but in short, the essence of Shor’s algorithm lies in its ability to transform a mathematical problem that is “almost unsolvable” on a classical computer into a “relatively easy-to-solve” periodic search problem on a quantum computer , potentially threatening the existing “private key-public key” cryptographic system of cryptocurrencies.
To give a more easily understandable example, you can easily turn a basket of strawberries (class private key) into jam (analogous to public key), but obviously you can’t reverse the jam back into strawberries. However, if a cheat code suddenly appears (analogous to quantum computing), it may be possible to achieve this in a convenient way (analogous to Shor’s algorithm).
Has the foundation of cryptocurrency been shaken?
If that’s the case, then isn’t cryptocurrency doomed?
Don’t panic. The quantum threat objectively exists, but the problem isn’t that urgent. There are two main reasons for this. First, there’s still time before a real threat arrives; second, cryptocurrencies can be upgraded to implement anti-quantum algorithms.
First of all, even if Scott’s prediction comes true before the 2028 election, it does not mean that the security of cryptocurrencies will be truly threatened; Vitalik’s statement is not saying that the foundation of Bitcoin and Ethereum will be shaken, but only pointing out a theoretical risk that exists in the long term.
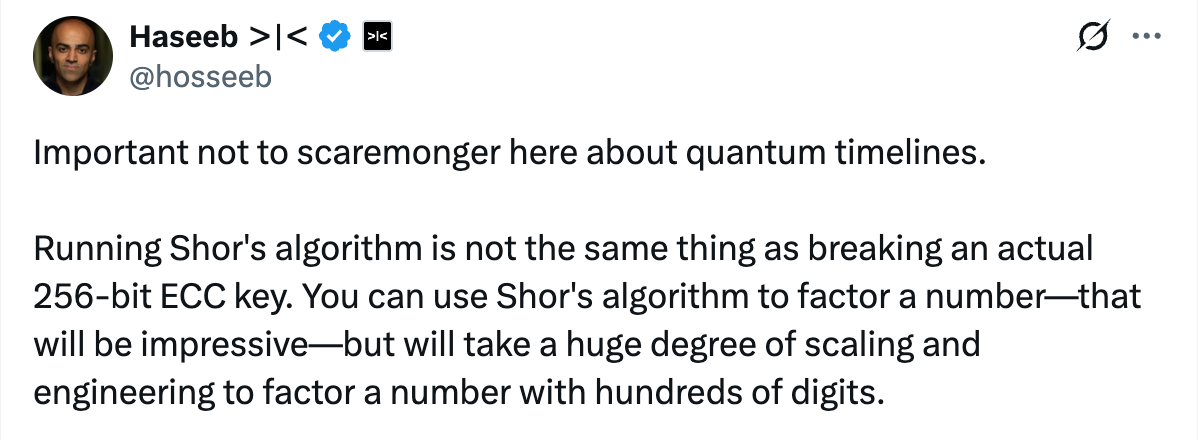
Dragonfly Managing Partner Haseeb explained that there’s no need to panic about the new timeline for quantum computing; running Shor’s algorithm is not the same as cracking a real 256-bit elliptic curve key (ECC key) . You can use Shor’s algorithm to crack a single number—that’s impressive enough—but factoring a number with hundreds of digits requires a much larger scale of computation and engineering capabilities… This is something to be taken seriously, but it’s not something that’s imminent.
Cryptocurrency security expert MASTR provides a clearer mathematical answer: cracking the Elliptic Curve Signature (ECDSA) currently used by cryptocurrencies such as Bitcoin and Ethereum requires approximately 2,300 logical qubits and 10¹² to 10¹³ quantum operations. With error correction, it would require millions or even hundreds of millions of physical qubits. However, currently implemented quantum computing only requires 100-400 noisy qubits, and its error rate is too high and its coherence time is too short— still at least four orders of magnitude away from the requirements for cracking the former.

As for the second point, cryptographers in the industry are also developing new post-quantum cryptography (PQC) algorithms that can resist quantum computing attacks , and mainstream blockchains have already prepared for this.
Back in March of last year, Vitalik wrote an article titled ” What if a quantum attack came tomorrow? How would Ethereum solve the problem? “, in which he mentioned the defensive effects of Winternitz signatures, STARKs, and other technologies against quantum threats, and even envisioned how Ethereum could be upgraded in an emergency.
Compared to Ethereum, Bitcoin may be less flexible in implementing upgrades, but the community has already proposed several potential algorithm upgrade solutions, such as Dilithium, Falcon, and SPHINCS+. Recently, with the increasing discussion surrounding this topic, Bitcoin OG Adam Back has also stated that post-quantum era cryptographic standards could be implemented long before a substantial quantum computing threat emerges.
In short, the quantum threat is like a “master key” hanging in the distance, theoretically capable of unlocking all current blockchains. However, the lock makers have already begun researching new locks that this master key cannot open, and are preparing to replace all the locks on all the doors before the master key is finished.
This is the objective reality regarding the quantum threat. We cannot ignore its progress, but there is no need to panic blindly because of it.
This article is sourced from the internet: With the resurgence of the quantum threat theory, has the foundation of cryptocurrency been shaken?Recommended Articles
编译 | Odaily 星球日报(@OdailyChina) 译者 | 叮当(@XiaMiPP) 编者按:由于 10.11 的黑天鹅闪崩,Ethena Labs 发行的稳定币 USDe 市值已降至 125 亿美元左右,较 7 天前的约 148.2 亿美元缩水超 20 亿美元。原因在于 USDe 在此次的加密货币大跌中一度与美元严重脱锚,在部分去中心化交易所最低跌至 0.62 美元,脱锚幅度高达 38%。虽然目前价格已恢复至 1 美元区间,但事件仍对用户信心造成了显著冲击。针对外界广泛关注的 USDe 脱锚传闻,Dragonfly 管理合伙人 Haseeb 出面发声(Dragonfly 为 Ethena 的投资方)。 以下为其原文内容: Ethena 真的脱锚了吗? 我看到这个周末市场大崩盘时,很多人都在讨论 Ethena 的 USDe 出现“脱锚”。传言说 USDe 一度跌至约 0.68 美元,随后才恢复。下面是大家都在引用的那张 Binance 价格图: 但经过过去几天对数据的深入分析,以及与多方人士交流后,现在可以确定:这个说法不正确。USDe 实际上并没有脱锚。 首先要理解的是,USDe 的主要流动性场所并不是中心化交易所(CEX),而是 Curve。 在 Curve 上,USDe 有数亿美元的深度流动性;而在包括 Binance 在内的各大交易所上,流动性只有几千万美元。 所以,如果你只看 Binance 上的价格图,会觉得 USDe 脱锚了。 但如果把 Curve 等其他主要交易场所的价格叠加上去,画面就完全不同了: 可以看到,虽然 USDe 在各个 CEX 上都出现了瞬时下跌,但并不一致。 Bybit 一度跌到 0.95 美元后很快回升,而 Binance 的跌幅却异常巨大,恢复时间也极长。 与此同时,Curve 上的 USDe 仅仅下跌了 0.3%。 那为什么会出现这种差异? 记住,当天整个市场都承受着极端压力——那是加密历史上规模最大的一次爆仓事件。 Binance 在这期间异常不稳定,做市商(MM)无法在平台内调仓,因为 API 接口频繁失效,充值和提现通道也几乎瘫痪。 结果是,没人能进场套利。这就好比 Binance 着火了,但所有通道都被堵死,消防员根本进不去。于是 Binance 内部火势蔓延,而其他地方由于有跨平台流动性桥接,火很快就被扑灭了。 (正如 Guy 在文中指出的,USDC 当时在 Binance 上也短暂“脱锚”了几美分,原因相同——并不是资产问题,而是流动性没法进来。) 所以,当交易所 API 出现不稳定时,交易所间价格差异极大也就不奇怪了——因为没人能补充库存。 但问题是:为什么 Binance 比 Bybit 价格偏离更严重? 答案有两方面: Binance 没有与 Ethena 建立主做市关系(Primary Dealer Relationship),无法在平台内直接铸造或赎回 USDe。Bybit 等交易所具备这种集成机制,使得做市商即便留在交易所内也能进行锚定套利。而在 Binance 上,做市商必须把资金转出 Binance,去链上进行 Ethena 套利,再转回来。在 API 失灵、市场崩盘的那一刻,没人会冒这个风险。 Binance 的预言机实现存在缺陷,导致误触发清算。健全的清算机制不会因瞬时闪崩而触发,但 Binance…







给你吧